RMM For Mobile Device Management: Complete Guide, Features and Details
In today’s hyper-connected world, mobile devices are no longer just tools for communication; they’re integral to business operations. From smartphones and tablets used by field service technicians to company-issued laptops for remote employees, the sheer number of mobile endpoints creates a complex management challenge. Neglecting mobile device management (MDM) can lead to security vulnerabilities, data breaches, and decreased productivity. That’s where Remote Monitoring and Management (RMM) solutions come into play, offering a comprehensive approach to overseeing and securing your mobile fleet.
While RMM is traditionally associated with managing desktops, servers, and network infrastructure, its capabilities have expanded to include robust mobile device management features. This evolution allows IT professionals to leverage a single platform to monitor, manage, and secure all endpoints, regardless of their operating system or location. Integrating MDM into your existing RMM framework streamlines IT operations, improves security posture, and ultimately, enhances business efficiency. It’s about having a centralized, unified view of your entire IT ecosystem.

This article will delve into the world of RMM for mobile device management, exploring its key features, benefits, and how it differs from standalone MDM solutions. We’ll also discuss the challenges of implementing RMM-based MDM and provide practical tips for choosing the right solution for your organization. Whether you’re a seasoned IT professional or just beginning to explore the possibilities of mobile device management, this guide will provide you with the knowledge you need to make informed decisions and optimize your mobile strategy.
What is RMM for Mobile Device Management?
RMM for Mobile Device Management extends the traditional capabilities of RMM platforms to encompass the specific needs of managing mobile devices. RMM, at its core, is a software solution designed to help IT service providers (MSPs) and internal IT departments remotely monitor, manage, and support their clients’ or organizations’ IT infrastructure. When MDM functionality is integrated, RMM becomes a powerful tool for managing a diverse range of devices, including smartphones, tablets, and even laptops, all from a single, centralized console.
Key Differences Between RMM and Standalone MDM
While both RMM and standalone MDM solutions aim to manage mobile devices, their core focuses and functionalities differ. Standalone MDM solutions are primarily focused on mobile device-specific tasks, such as:
- Mobile Device Enrollment: Securely enrolling devices into the management system.
- Policy Enforcement: Enforcing security policies, such as password requirements, encryption, and app restrictions.
- App Management: Distributing, updating, and managing mobile applications.
- Remote Wipe: Remotely wiping data from lost or stolen devices.
RMM, on the other hand, provides a broader spectrum of IT management capabilities, including:
- Remote Monitoring: Monitoring device health, performance, and security status.
- Patch Management: Automating the deployment of software updates and security patches.
- Remote Access: Providing remote access to devices for troubleshooting and support.
- Automation: Automating routine IT tasks to improve efficiency.
- Reporting and Analytics: Generating reports on device usage, security compliance, and performance.
Therefore, RMM with MDM capabilities offers a more holistic approach, integrating mobile device management with other IT management functions. This integration simplifies IT operations, reduces the number of tools required, and provides a single pane of glass for managing the entire IT environment.
Key Features of RMM for Mobile Device Management
A robust RMM solution with integrated MDM should offer a comprehensive set of features to effectively manage and secure mobile devices. Here are some of the key features to look for:
Device Enrollment and Provisioning
This feature allows you to easily enroll new devices into the management system, typically through methods like over-the-air (OTA) enrollment, Apple Business Manager (ABM), or Android Enterprise. Automated provisioning allows for pre-configuring devices with necessary apps, settings, and security policies, ensuring consistent configurations across all devices. This is crucial for streamlining onboarding and minimizing manual configuration efforts.
Mobile Device Configuration and Policy Management
This feature enables you to configure device settings, such as Wi-Fi, VPN, email, and security policies, remotely. You can enforce password complexity requirements, restrict access to certain websites or apps, and configure device encryption. Granular policy management allows you to create different policies for different user groups or device types, tailoring security and access controls to specific needs.
Application Management
RMM with MDM should allow you to manage mobile applications on enrolled devices. This includes:
- App Distribution: Deploying apps to devices silently and automatically.
- App Updates: Managing app updates to ensure users are running the latest versions.
- App Restrictions: Restricting the installation or use of certain apps.
- App Blacklisting/Whitelisting: Creating lists of approved or prohibited apps.
Security Management
Security is paramount in mobile device management. Key security features include:. Many businesses find that streamlining processes is essential for growth, and ERP is often considered as a key element in that effort
.
- Remote Wipe: Remotely wiping data from lost or stolen devices to prevent unauthorized access.
- Remote Lock: Remotely locking devices to prevent access.
- Geolocation: Tracking the location of devices to help recover lost or stolen devices.
- Threat Detection: Identifying and mitigating security threats, such as malware or phishing attacks.
- Data Loss Prevention (DLP): Preventing sensitive data from leaving the device or network.
Remote Monitoring and Support
RMM allows for real-time monitoring of device health, performance, and security status. This includes monitoring battery life, CPU usage, storage capacity, and network connectivity. Remote support capabilities enable IT staff to remotely access devices for troubleshooting and support, reducing the need for on-site visits and improving resolution times.
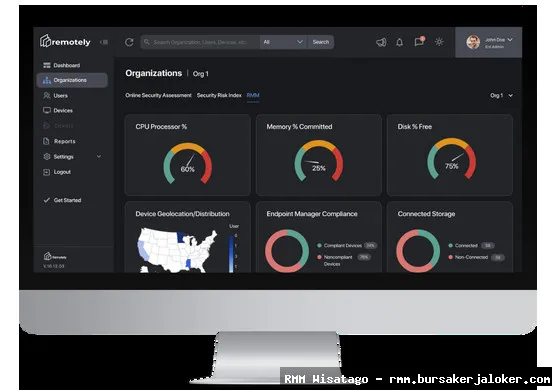
Reporting and Analytics
Comprehensive reporting and analytics provide insights into device usage, security compliance, and performance. Customizable reports can be generated to track key metrics and identify trends, allowing you to make data-driven decisions about your mobile device management strategy. These reports can also be used for compliance auditing and reporting.
Benefits of Using RMM for Mobile Device Management
Implementing RMM for MDM offers numerous benefits for organizations of all sizes. Here are some of the key advantages:
Centralized Management
One of the biggest advantages is the ability to manage all endpoints, including desktops, servers, and mobile devices, from a single, centralized console. This eliminates the need for multiple management tools and simplifies IT operations.
Improved Security
RMM with MDM helps improve security by enforcing security policies, managing app permissions, and providing remote wipe capabilities. Real-time threat detection and data loss prevention features help protect sensitive data from unauthorized access or loss.
Increased Productivity
By automating routine IT tasks, such as software updates and device configuration, RMM with MDM frees up IT staff to focus on more strategic initiatives. Remote support capabilities enable faster troubleshooting and resolution, minimizing downtime and improving user productivity.
Cost Savings
Consolidating IT management tools into a single RMM platform can lead to significant cost savings. Reduced IT staff workload, improved efficiency, and fewer security incidents contribute to a lower total cost of ownership.
Enhanced Compliance
RMM with MDM helps organizations meet compliance requirements by providing detailed reporting and auditing capabilities. Automated policy enforcement ensures that devices are configured according to industry best practices and regulatory standards.
Challenges of Implementing RMM for Mobile Device Management
While RMM for MDM offers many benefits, there are also some challenges to consider during implementation:
Complexity
Implementing and configuring RMM with MDM can be complex, especially for organizations with limited IT resources. Proper planning, training, and documentation are essential for a successful implementation. Consider engaging with an experienced MSP or IT consultant to assist with the implementation process.
Integration
Integrating RMM with MDM with existing IT systems, such as Active Directory or cloud services, can be challenging. Ensure that the RMM solution supports the necessary integrations and that you have a clear understanding of the integration process.
User Adoption
Getting users to adopt new mobile device management policies and procedures can be difficult. Clear communication, training, and support are essential for ensuring user compliance. Address user concerns and provide clear explanations of the benefits of MDM.
Security Risks
While RMM with MDM helps improve security, it can also introduce new security risks if not properly configured and secured. Implement strong security measures, such as multi-factor authentication and regular security audits, to protect the RMM platform and managed devices.
Choosing the Right RMM Solution for Mobile Device Management
Selecting the right RMM solution with MDM capabilities is crucial for achieving your mobile device management goals. Here are some factors to consider:
Features and Functionality
Evaluate the features and functionality of different RMM solutions to ensure that they meet your specific needs. Consider features such as device enrollment, policy management, app management, security management, and remote support.
Platform Support
Ensure that the RMM solution supports the mobile operating systems that you need to manage, such as iOS, Android, and Windows. Check for compatibility with different device types, such as smartphones, tablets, and laptops.
Scalability
Choose an RMM solution that can scale to meet your growing needs. Consider the number of devices you need to manage now and in the future, and ensure that the solution can handle the load.
Security
Security is paramount. Evaluate the security features of the RMM solution, such as encryption, multi-factor authentication, and security audits. Ensure that the vendor has a strong security track record and complies with industry best practices.
Pricing
Compare the pricing models of different RMM solutions and choose one that fits your budget. Consider factors such as the number of devices you need to manage, the features you need, and the level of support you require. Look for solutions that offer flexible pricing options.
Vendor Reputation and Support
Choose a reputable vendor with a proven track record and excellent customer support. Read reviews and testimonials to get an idea of the vendor’s reputation. Ensure that the vendor offers comprehensive training and support resources.
Conclusion
RMM for mobile device management offers a powerful and efficient way to manage and secure your mobile workforce. By integrating MDM capabilities into your existing RMM framework, you can streamline IT operations, improve security posture, and enhance business productivity. While there are challenges to consider during implementation, the benefits of RMM with MDM far outweigh the risks. By carefully evaluating your needs and choosing the right solution, you can unlock the full potential of mobile device management and empower your organization to thrive in the mobile-first world.
The key takeaway is that a unified approach to IT management, encompassing both traditional infrastructure and mobile devices, is essential for modern businesses. RMM provides that unity, offering a single platform to monitor, manage, and secure your entire IT ecosystem. Embrace RMM for MDM and take control of your mobile destiny.
Ultimately, the success of your RMM for MDM implementation hinges on careful planning, clear communication, and a commitment to continuous improvement. Stay informed about the latest trends and technologies in mobile device management, and adapt your strategy as needed to meet the evolving needs of your organization. With the right approach, RMM for MDM can be a game-changer for your business.
Frequently Asked Questions (FAQ) about RMM for mobile device management
What are the key benefits of using a Remote Monitoring and Management (RMM) platform specifically for mobile device management (MDM) within my organization?
Implementing an RMM platform for mobile device management offers numerous key benefits for organizations. Firstly, it provides centralized control and visibility over all enrolled devices, allowing administrators to remotely monitor device health, performance, and security status. This proactive monitoring helps identify and resolve potential issues before they impact productivity. Secondly, RMM enables efficient patch management and software updates, ensuring that all mobile devices are running the latest versions of operating systems and applications, thus reducing vulnerability to security threats. Thirdly, features like remote wipe and lock provide essential security measures in case of device loss or theft, protecting sensitive corporate data. Finally, RMM solutions often include automation capabilities, streamlining tasks such as configuration management, policy enforcement, and application deployment, significantly reducing IT workload and improving efficiency.
How does an RMM solution help in securing corporate data on employee-owned mobile devices (BYOD) when used for mobile device management?
RMM solutions play a crucial role in securing corporate data on employee-owned mobile devices within a Bring Your Own Device (BYOD) environment. By implementing mobile device management (MDM) through an RMM, organizations can enforce security policies like strong passwords, device encryption, and screen lock timeouts. RMM allows for the creation of separate containers on the device, isolating corporate data from personal apps and information, preventing data leakage. In cases of device loss or employee departure, administrators can remotely wipe the corporate container without affecting the user’s personal data. Furthermore, RMM can monitor device compliance with security policies, block access to sensitive resources for non-compliant devices, and provide real-time alerts about potential security breaches. This layered approach provides a robust security framework for managing BYOD devices.
What specific reporting and analytics features should I look for in an RMM platform to effectively manage and optimize our mobile device fleet?
When choosing an RMM platform for mobile device management, it’s essential to consider the reporting and analytics features it offers. Look for a platform that provides comprehensive reports on device inventory, including hardware specifications, operating system versions, and installed applications. Detailed security reports are crucial for identifying devices with vulnerabilities or non-compliant configurations. Performance monitoring reports should track CPU usage, memory consumption, and battery health to proactively address performance issues. Application usage reports can help optimize application deployment and identify unused or underutilized apps. Furthermore, compliance reports demonstrating adherence to security policies and industry regulations (e.g., HIPAA, GDPR) are vital. The RMM should also offer customizable dashboards and alerts to provide real-time visibility into the health and security of the mobile device fleet, enabling proactive management and informed decision-making. Effective reporting and analytics are key to optimizing mobile device performance and security.